SS7 Vulnerability Explained
What is SS7?
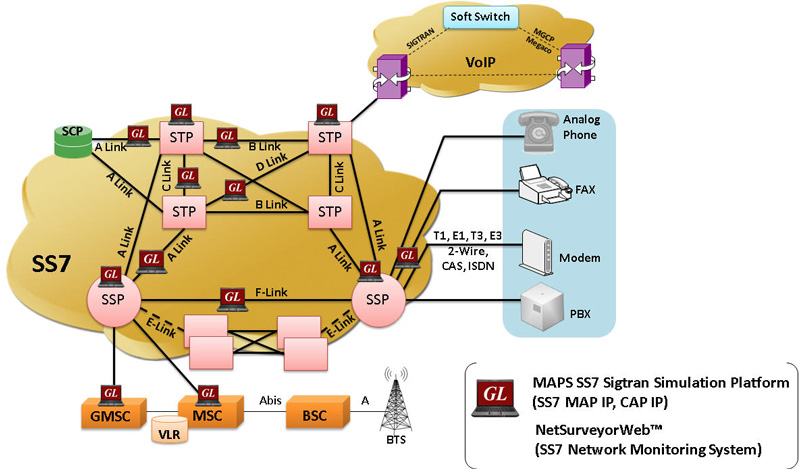
Signalling System No 7 (SS7) is an international telephone signalling protocol which was developed in 1975 . SS7 is designed to operate in two modes: associated mode and quasi-associated mode. The diagram shows a basic structure of the network. Customers are connected at End Office. It is directly connected to service switching point (SSP) which converts the dialed digits to signalling messages. Then the SS7 network routes the signals to its destination using signal transfer point (STP).
The vulnerability
Signalling System No 7 (SS7) vulnerability is found in the mobile network which allows hackers to read your text messages, listen to your calls or track your mobile location. It was first discovered in 2014 where some German researchers demonstrated the exploit. Many people think that it had been known to many government secret agencies but was not made public for security reasons.
“It’s like you secure the front door of the house, but the back door is wide open,” said Tobias Engel, one of the German researchers.
Implications for the user
This flaw can be used to bypass 2 step authentication. For now, it is better to switch to 2 step authentication using emails . Last year, bank accounts of some German citizens were drained where a hacker installed a malware to get access to user's bank account username and password and used SS7 vulnerability to read the OTP.
Protection against the flaw
If possible, it is better to use encrypted chat applications like telegram. Whatsapp is not a good alternative since a hacker can still use the flaw to install whatsapp in his phone and read the OTP on your phone. For calls, it is better to use calls over Wifi or data. For avoiding tracking of location, there is no way except to keep it on airplane mode or turn your mobile off.
The Fix
SS7 vulnerability can be fixed if telecom companies add a filter in the network. Although it wont completely fix the vulnerability but it will stop most of the unauthorized users for getting into the network. Adding a layer of encryption would also help but it would take telecom companies months to years to do the same. This is because it would require building SS7 with encryption from scratch.
Follow us on Facebook:- Facebook.com/VAPTHacker
LinkedIn:- https://www.linkedin.com/in/rohankalra97/
Twitter:- https://twitter.com/rohankalra97

This comment has been removed by the author.
ReplyDeleteA pleasant post shared. Thanks for sharing an amazing post with us.
ReplyDeleteSecurity Officer
Great post!!
ReplyDelete"SOC
Vulnerability assessment
ISO 27001 Compliant Companies In India"
This comment has been removed by the author.
ReplyDeleteThis comment has been removed by the author.
ReplyDelete